As a netizen, how particular are you when it comes to safeguarding your personal information, or that of your clients?
Research says: not so much.
Brute force attacks have been a common occurrence on the internet for a long time now. Large scale attacks have only shown an upward trend in recent times. Moreover, the success rate of a brute force attack is also high.
The main reason why brute force attacks work is that people use weak passwords which aren’t hard to guess.
80% of hacking-related breaches were because of weak passwords.
In this article, we’re going to cover all ground on brute force attacks and how you can prevent them.
Table of Content:
- What is a brute force attack?
- Types of brute force attacks
- Why do hackers launch a brute force attack?
- Popular brute force attack software
- Brute force attack example
- How can you Prevent Brute Force Attacks?
- Conclusion
1. What is a brute force attack?
A brute force attack is a hit-and-trial method of cracking another person’s username, password, or PIN for a website. It involves trying out different password combinations until you get the right one and gain access to another user’s account.
Sounds impractical right?
Passwords of today are at least 8 characters long and usually contain both uppercase and lower case characters, along with numbers and symbols. If you do the math, you’ll see that there are a Million plus combinations one has to try in order to nab one password. So how can a hacker possibly think, let alone try to crack one password in their lifetime?
Well, they don’t actually do it manually.
A hacker will run a script or a code, or use a bot that will keep trying combinations till they hit the right one. The only difference is, bots can be configured to guess much faster. And so a hacker can easily crack a password within 6 hours of running the code.
And like I mentioned above, It doesn’t help that users mostly set weak passwords that automated software can sometimes guess in seconds.
The time taken to crack a password depends on the resources available with the hacker, the power of the code that he/she runs, and the security level of the account he/she is trying to enter into.
Taking these factors into account, it may take a few hours or sometimes days and weeks to find the right password. But history is evidence enough that the success rate of a brute force attack is high.
2. Types of brute force attacks
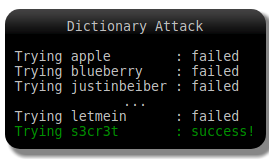
2.1 Dictionary Attack
This type of attack uses a certain list or ‘dictionary’ of common passwords. It doesn’t blindly try on different combinations of all the characters that can be used in a password. Instead, possible passwords are listed (like words in a dictionary) and tried on till the right one is found.
2.2 Simple Brute force Attack
A simple brute force attack is exactly what we discussed in the first section. All possible combinations of different characters, numbers, and symbols are tried until the right one is found. It works on websites or files where there’s no limit to how many attempts can be made.
2.3 Hybrid Brute Force Attack
A hybrid brute Force attack is a combination of a dictionary attack and a simple brute force attack. While dictionary attacks use some logic behind what passwords should be tried, simple attacks randomly try combinations.
In a hybrid brute force attack, the attacker tries different combinations of numbers and symbols along with words from a pre-listed dictionary in order to crack the password.
2.4 Credential Stuffing
Once an attacker gets hold of a username-password pair, he/she might try to use it on different websites. This type of attack exploits the fact that a lot of people use the same username-password pair on various websites.
2.5 Reverse Brute Force attack
A reverse brute force attack tries different usernames with a previously obtained password to gain access, instead of trying different password combinations with one username.
3. Why do hackers launch a brute force attack?
Brute force attacks can be used to:
- Steal sensitive information from a website
- Shut down a website completely
- Infect it with malicious code to gain long term benefits
- Use the website to post or publish content
- Sell the information acquired to some third party
IT teams in charge of security also use brute force attacks in order to check the strength of their systems.
4. Popular brute force attack software
Hackers are always backed by automated software tools that use algorithms to crack passwords. Some of the popular software tools are:
4.1 John the Ripper
One of the most popular and fastest password cracking tools out there, John the Ripper can perform both dictionary-based and simple brute force attacks. It comes pre-installed with a list of passwords, and can automatically detect the type of hashing used in a password.
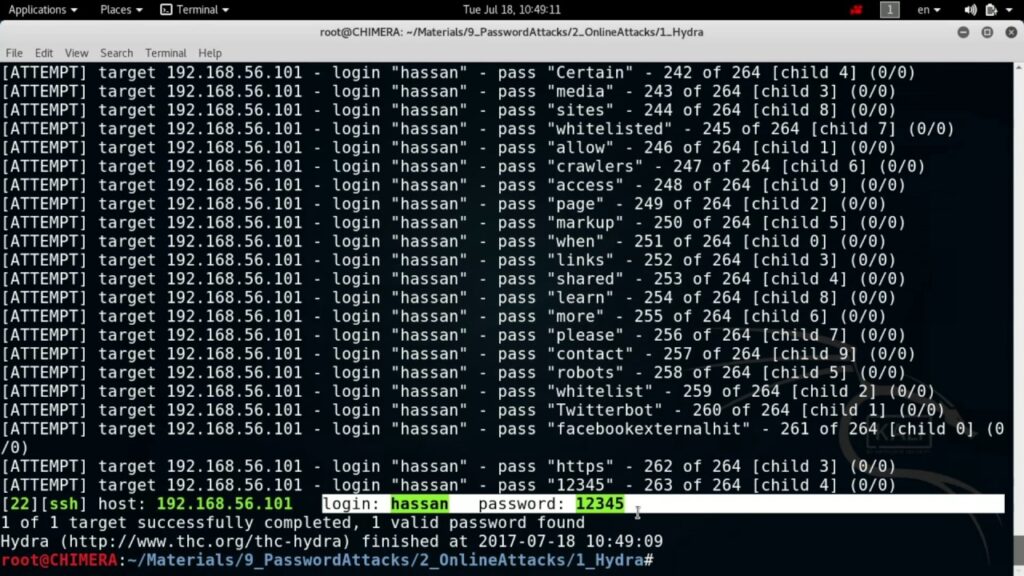
4.2 THC Hydra
THC Hydra can attack 50 protocols (HTTP, SMB, FTP, etc) and many operating systems using dictionary attacks. It is the oldest brute attack software you can find, and IT specialists often use it to identify the strength of their client systems.
4.3 Aircrack-Ng
Aircrack-Ng is mainly used to breach WiFi networks. It focuses on monitoring, testing, attacking, and cracking WiFi network security.
4.4 Hashcat
It can perform simple brute force attacks, hybrid attacks, dictionary attacks, and rule-based attacks. It is a CPU based password-guessing software, that supports five modes of attack for over 200 optimized hashing algorithms.
Other popular brute force attack software are:
- L0phtCrack
- Ncrack
- Cain & Able
- Rainbow Crack
- SAMInside
5. Brute Force Attack Examples
Let’s take real-life examples to understand the gravity of brute force attacks and how dangerous they can be:
1.Magento: in March 2018, around 1000 open source accounts were compromised due to brute force attacks. The attackers used those accounts to steal credit card information and cryptocurrency mining.
2. Alibaba: TaoBao, an Alibaba e-commerce site was struck by a massive brute force attack, affecting around 21 million accounts on the website. The success rate was one in five. Moreover, the attackers had used servers lent by Alibaba itself to launch the attack!
3. Github: In 2013, Github also came under a brute force attack. The attackers had used approximately 41,000 IP addresses to make login attempts. While it isn’t known how many accounts exactly were compromised, the attack was still one of the largest in history.
4. Club Nintendo: A community forum for gamers, Club Nintendo saw 25,000 of its user accounts compromised in 2013. Hackers had to make 15 million attempts in order to breach these many accounts.
Interesting read: How a Hacked Website 2X its Sales in 30 Days
6. How can you Prevent Brute Force Attacks?
There are a lot of measures you can take in order to ensure that any brute force attack on your system isn’t successful.
6.1 Use Strong Passwords
When a hacker takes the brute force approach, the weaker your password is, the easier it will be to crack. Make sure that password you set is:
- Unique: This means it hasn’t been set on any other website with your username. If you use the same password for many websites, then hackers can use it to breach other accounts you have on the web and steal more information.
- Long: a four-digit pin (using only numbers) can have 10,000 possible combinations. Using software, this pin can be cracked in a matter of minutes. Similarly, to crack an 8 digit pin, it could take a day or two to crack a password even if you’re using software. Which is why it’s advisable to set a password that has around 15-20 characters to make guessing harder.
- Less obvious: people usually use birth dates, their own names, names of things or people close to them, etc in their passwords. These passwords are very easy to guess as it’s easier to find personal information nowadays. This is why you should go for something random which might not be directly related to you but is easy to recall. Basically, avoid common terminology and numerical combinations as much as you can.
6.2 Limit Login Attempts
The success of a brute force attack depends on the number of times attempts can be made to guess a password before the hacker gets it right. If you limit login attempts per user, the hacker’s chance of breaking in will reduce considerably.
Remember that different accounts and IP addresses can be used for each attempt. A common practice is to temporarily block an IP or account from attempting to log in after 4 or 5 failed attempts. Each time 4-5 failed attempts have been made, you can increase the temporary block duration. This will buy you time and your systems will be able to detect bots and block them before they can do damage.
6.3 Use 2-Factor Authentication
2FA’s are quite common these days. After you’ve entered the username and password to an account, you have to enter another code or pin that only you can access. You usually receive these One Time Passwords (OTPs) on your phone or email.
Sometimes double verification could also mean fingerprint scans or face detection once you’ve entered your password.
This adds an extra layer of security and hackers can’t access your account just by cracking your password.
6.4 Use Captcha
Hackers can’t execute a brute force attack without bots. Adding Captcha to your login page can make it difficult for bots to pass, as its challenges are designed for humans to solve. It’s now used on all pages where users have to enter sensitive information.
6.5 Web Application Firewall (WAF)
A WAF is a thick layer of security that detects unwanted traffic and blocks it before can reach your network. For example, we use Sucuri firewalls on our servers to protect our client websites and their data.
Apart from the techniques we mentioned above, our Sucuri WAFs use IP whitelisting, signature detection, and bot & scan blocking to prevent brute force attacks. Bots attempting to log in are proactively detected and blocked, without affecting the normal traffic to our client websites.
7. Conclusion
Brute force attacks are common and should not be taken lightly. As we’ve seen, even big companies aren’t immune to account break-ins. We should take all possible measures to minimize their chance of succeeding.
If you have any more questions regarding a brute force attack, talk to experts or mention in the comments below!

Divya loves writing and is passionate about marketing. When not trying to hone her skills, you’ll find her either reading or binging on TV shows.





0 Comments