Cyber-attacks have surged dramatically in recent years. eCommerce websites, in particular, run a high risk of vicious online attacks as they house sensitive customer information. Store owners need to do everything in their power to tighten their website’s security and minimize the risk of cyberattacks.
It is estimated that approximately $6 trillion is expected to be spent globally on cybersecurity by 2021.
A WAF or Web Application Firewall is a powerful layer of security that sits between your website and outside traffic. But what is its exact purpose? And how does it work? In this article, we will dive deep into everything you need to know about web application firewalls, their functions, and their types.
Table of Content:
- What is WAF (Web Application Firewall)?
- Types of Attacks a WAF Protects Against
- What does a WAF do & how does it work?
- Functions of a Web Application Firewall
- Types of Web Application Firewalls
- How to Choose the right WAF?
What is WAF (Web Application Firewall)?
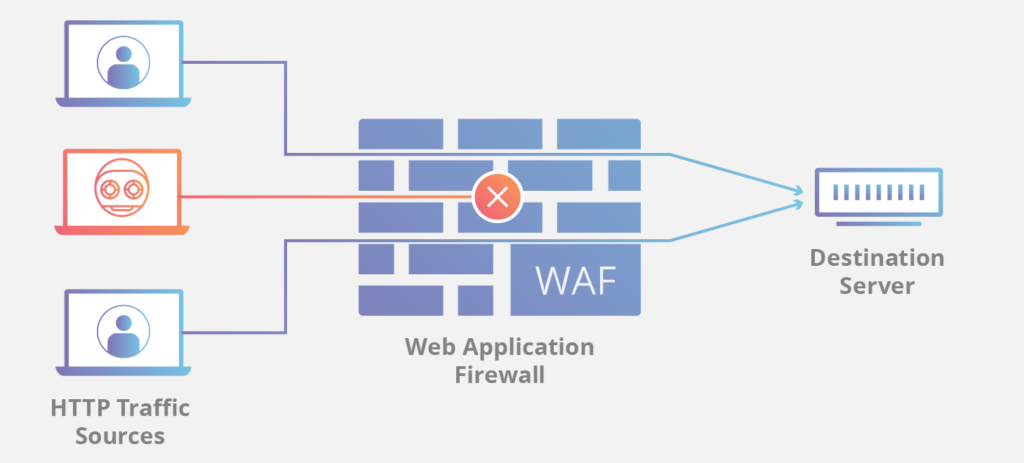
A WAF or Web Application Firewall is the protective barrier between a web application (or its server) and the internet. In simple terms, It monitors the traffic hitting website servers with requests, and filters out the ones with malicious intent. WAF comes under the OSI (Open Systems Interconnection) protocol as a layer 7 defense.
Different types of online attacks target different layers (a total of 7) in the OSI model, which is why a WAF is not designed to protect against all types of cyberattacks. A WAF is not an all-in-one solution, but rather one piece in a host of tools required to safeguard websites today.
Please note: it easy to confuse a WAF with a traditional firewall. A WAF is a type of firewall, aimed to monitor the traffic requests made to your application and the data within. Whereas traditional firewalls can be of various types, for example, network firewalls, packet filtering, stateful firewalls, etc.
Types of Attacks a WAF Protects Against
Typically, a Web Application Firewall will protect your online site against the following types of attacks:
- DDoS attacks: overwhelming an application’s servers by sending copious amounts of traffic and requests, in order to bring a server down.
- SQL Injection: executed on the contact and submissions forms of a website. Hackers insert harmful SQL codes into the user fields in the form of requests and queries. This helps them gain access to the website’s backend and steal information.
- Cross-Site Scripting (XSS): attackers use loopholes and gaps within the application to insert malicious codes/scripts which get activated when the users load the website.
- Zero-day attacks: these attacks are completely unexpected, and reveal security gaps after the attack has been executed and the damage has been done. To orchestrate these attacks, perpetrators spend some time snooping on the application in order to identify vulnerabilities and target them.
- Stealth commanding: an attack on the operating system of the application’s server.
- Man-in-the-middle attacks: the attackers place themselves in the middle of the two parties ( i,e., the application, and the user) and impersonate one of the two. Can be organized through IP spoofing, DNS poisoning, SSL hijacking, etc.
- Malware: application vulnerabilities or hacking attacks like Phishing are used to infect the website with malware like Trojan, ransomware, spyware, rootkits, etc.
- Defacements: the assailants infiltrate a website and change its contents to display astonishing or offensive information that might be detrimental to the website’s reputation.
Interesting read: Brute Force Attack: All you Need to Know
What does a WAF do & how does it work?
So how exactly does a WAF work to prevent cyber attacks?
A WAF is basically a reverse proxy stationed at the top of your application to improve its performance and security. Firewalls can be deployed as hardware devices, server-side software, or cloud-based services.
Like I mentioned earlier, a Web Application Firewall is designed to defeat only certain types of attacks. It works on a set of ‘policies’, which tell the firewall which loopholes, suspicious traffic behavior, vulnerabilities to look for. When a typical hacking behavior is detected, the WAF follows a series of prescribed actions to counter or prevent attacks.
The WAF scans incoming HTTP requests for questionable behavior. It analyses the headers and contents of a request. Smart WAFs further challenge these requests and ask for proof that a human has launched the request and not a bot. Fraudulent traffic is immediately blocked or further tests are conducted to prevent harmful bots or computer programs from proceeding.
A firewall also scans web applications for loopholes that hackers could exploit and immediately conducts patching upon discovery. It automatically blocks malicious actors from finding these loopholes, giving administration personnel an adequate time window to stitch up all vulnerabilities.
A Web Application Firewall can be configured according to two security models:
- Whitelisting model (positive security model): Under this configuration, the WAF allows only approved traffic to access the application. Thus only a limited group of users will be allowed, and all other traffic will be blocked. This model works best when your website is in its testing phase and not open for the general public.
- Blacklisting model (or negative security model): This model takes a block-first approach. The WAF is configured to block specific vulnerabilities, malicious actors, and attack signals. For example, you can direct a firewall to block IP addresses that arbitrarily start sending unusually high traffic.
A hybrid model performing the functions of both the whitelisting and blacklisting model can also be employed.
A WAF’s policies and models can be modified according to the risk profile and security requirements specific to your website. You need smart administration or hosting services that will structure your WAF into a full-proof security package that keeps attackers are bay.
Functions of a Web Application Firewall

Let’s get a bird’s eye view of the purposes or benefits a Web Application Firewall serves.
1. DDoS Mitigation
In a DDoS attack, the hacker gets hold of multiple servers to form a ‘botnet’ and sends overwhelming traffic to the target website. The botnet sends multiple requests to the application server in order to bring the site down. A WAF detects these botnets and blocks them before they can reach the website’s server.
2. Content Delivery Network (CDN)
WAF boosts the speed of your website with the help of a content delivery network or CDN. It caches your website on the CDN, and content is delivered through the location or point of presence nearest to the visitor. WAFs have known to increase the load time of websites by approximately 70%.
3. Signature Blacklisting
All online entities have some form of digital signatures that make them identifiable. When an entity or an HTTP request is found to be malicious, its signature is added to a WAFs blacklist. The malicious actor gets blocked before it reaches your website, and the same entity cannot attack you again.
4. Correlation Engine
A correlation engine monitors and learns the website’s normal behaviour, and then regularly compares it with how the application is behaving in real-time. If any discrepancies are detected, administration is warned immediately.
5. Application Profiling
All websites and applications vary profoundly in terms of structure and functioning. A WAF understands a website’s anatomy and how it functions normally. On the basis of this profile, the WAF looks for suspicious behavior, loopholes, and threats that might be the result of an infiltration.
Types of Web Application Firewalls

Web Application firewalls can be deployed in three ways:
1. Network-based Firewalls
Network WAFs are mostly hardware-based. Meaning, a hardware appliance is installed on your server and to monitor data packets, its metadata, and actual content associated with it.
Network WAFs can be expensive, as they are installed locally. They require storage of physical equipment and constant maintenance. But the upside is that these firewalls are fast as they are installed locally. Other types of WAFs may suffer from data latency.
Note: network-based WAFs and network firewalls are two different types of firewalls. While a network firewall focuses only on network connection requests, a network-based WAF is its advanced version that looks into the actual data being transmitted. It offers more superior threat detection by using machine learning and other intelligent techniques.
2. Host-Based Firewalls
Host-based firewalls are installed into the application’s software. It can be installed as a plugin or external software. These types of WAFs are a little complex in nature and require advanced knowledge of operation and configurations. Since they are localized, you will have to bear the resource cost and storage responsibility.
3. Cloud-based WAFs
Like everything else that is cloud-based, WAFs installed on a cloud platform will help you save money on resources and maintenance costs as they are not installed locally. Cloud-based firewalls offer mobility and give more reliable performance. They can be installed and configured effortlessly as well. Examples include Sucuri or Cloudflare firewalls.
4. Open Source WAFs
These firewalls can be accessed for free, but will require some dedicated service for deployment, configuration, and maintenance. If you don’t want to depend on third parties and have an IT team of your own, then you can look into this option.
How to Choose the right WAF?
Now that you know everything about what is WAF, how it works, the purposes it serves, and the various ways it is deployed in, it’s time to make a choice!
If you have the resources to fully manage your WAF on your own, then you can go for network-based or host-based firewalls. These firewalls will be relatively expensive and will take up your resources. If however, you want minimal interaction with your WAF side of issues, then it is recommended to go for cloud-based WAFs. They are easy to set up and configure, and managing them is the provider’s headache.
The best choices at your disposal will be revealed by your host, based on the hosting services you have opted for. At Webscoot we offer Sucuri and Cloudflare firewalls to our clients. We manage and optimize those for high-quality performance and reduced costs.
If you have any queries or feedback, do mention in the comments below!
Read next: Magento Security: Ultimate Guide for Magento Merchants

Divya loves writing and is passionate about marketing. When not trying to hone her skills, you’ll find her either reading or binging on TV shows.





Great article Divya I was looking for web application firewall meaning and found this really helpful piece of content, Is working of web application firewall in AWS is different from web application firewall?
Also how it can be differentiated from web application firewall in azure?